Cyber Security Solutions
Home Cyber Security Solutions

Our Capabilities
External Attack Surface Management
Our EASM platform help you identify, prioritize and eliminate the most critical cyber risks to your organization. Automatically discovers your organization’s structure and internet-exposed assets, eliminating blindspots caused by unknown or forgotten infrastructure and giving security and IT operations teams a single, complete inventory of your digital assets.
Our Capabilities
Digital Risk Protection
Our Digital Risk Protection solution is an all-in-one platform that uses the benefits of machine learning and neural networks to automatically monitor a company’s digital footprint, detect violations, prioritize and initiate appropriate takedown tactics. The solution offers full-fledged protection against risks that lie beyond the company’s perimeter, including but not limited to phishing, scams, piracy, and data leaks, fake partnership, fake mobile apps.

Our Capabilities
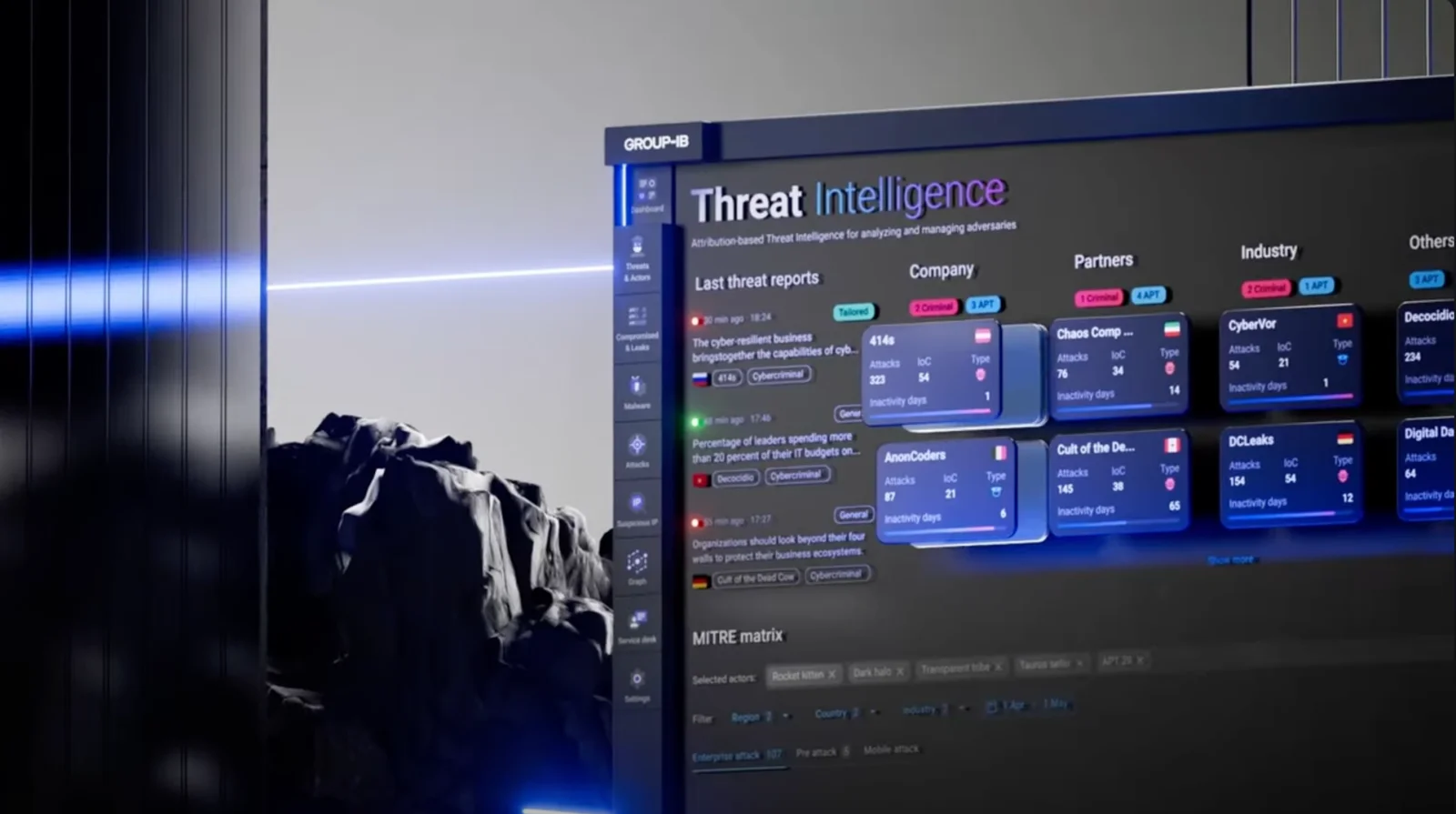
Global Threat Intelligence
Our Sources of Threat Intelligence provides unparalleled insight into your adversaries. Integrate the intelligence to maximize the performance of every component of your security ecosystem.
Equipping your team with strategic, operational and tactical intelligence streamlines security workflows and increases efficiency.
Our Capabilities
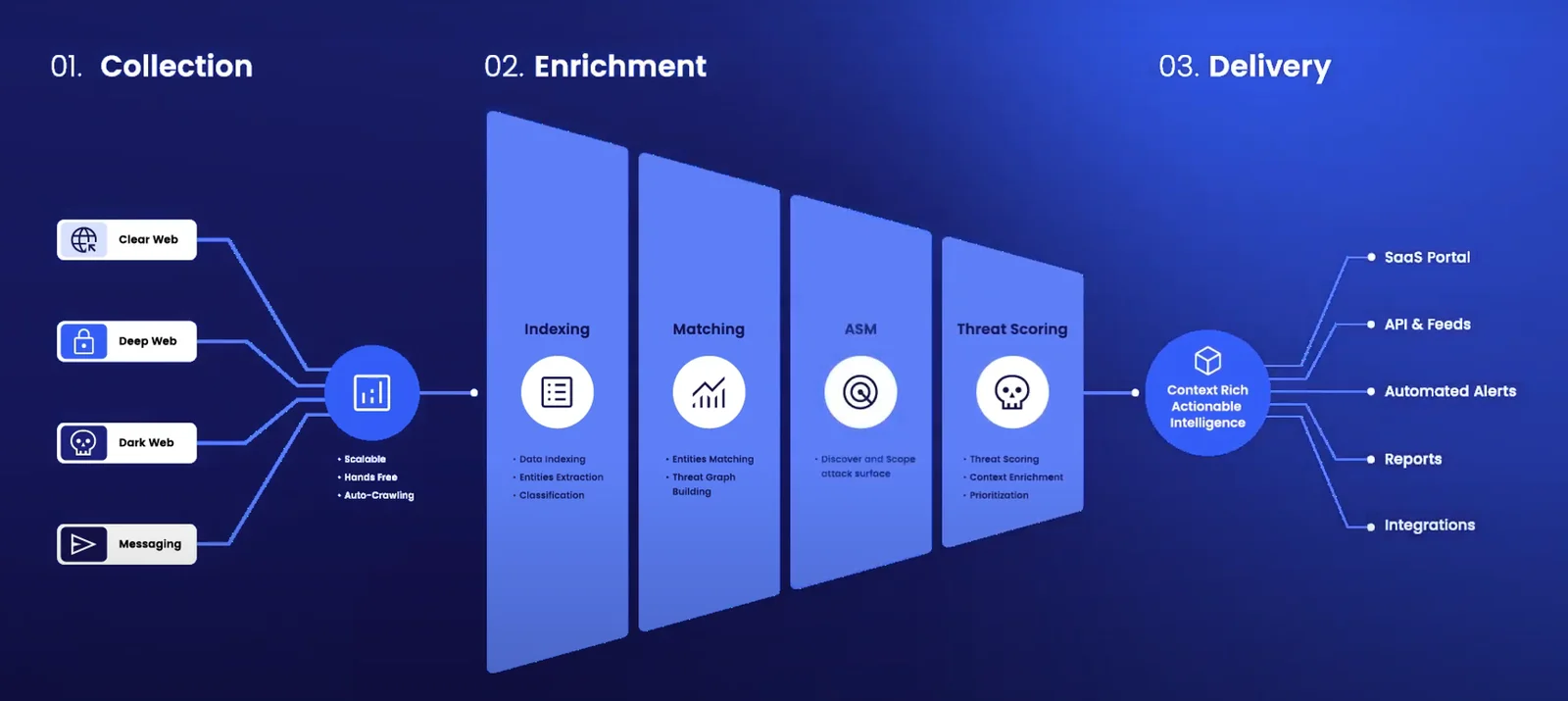
Darkweb/Deepweb Reconnaissance
Using advanced machine learning we covertly extract threat actor data from clear, deep and dark web sources including limited-access dark web forums and markets, invite-only messaging groups, code repositories and paste sites. We enrich this data with context to provide security teams with real-time comprehensive insight into the nature and source of each threat so they can detect and prevent cyber attacks before they happen. Set up customizable alerts to notify you of compromised employee credentials or customer data leaked on the deep and dark web. Search our data collection across multiple sources including instant messaging apps, IRC chats and limited-access dark web forums and marketplaces. Receive a breakdown of leaked credit cards by BINs, geography or issuer.
Our Capabilities
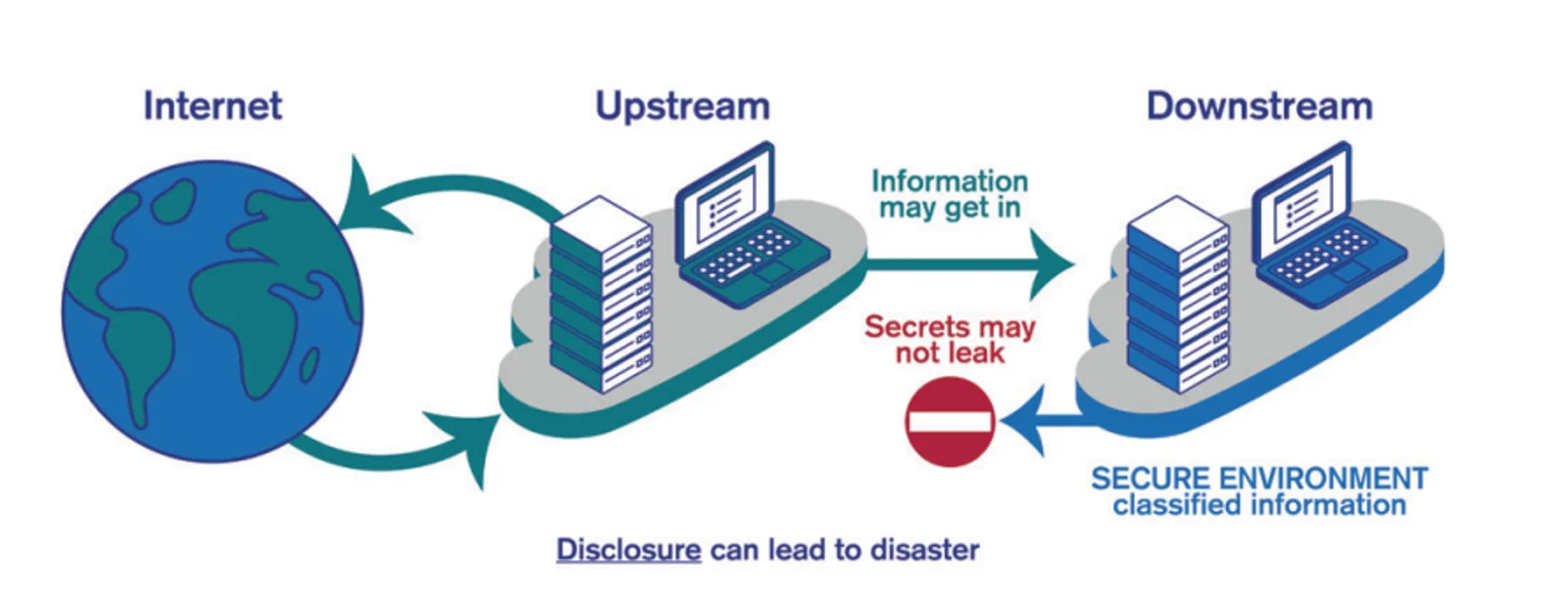
Network Security
Our DataDiode prevents data from leaving the high secure network by ensuring a guaranteed one-way network connection. This automates and streamlines the process of transporting information to confidential networks at the same time lifting the security levels to new heights, by securely and smoothly transferring information in real time. This way, you will have immediate access to the most recent acquired intelligence in your confidential environment.
Our Capabilities
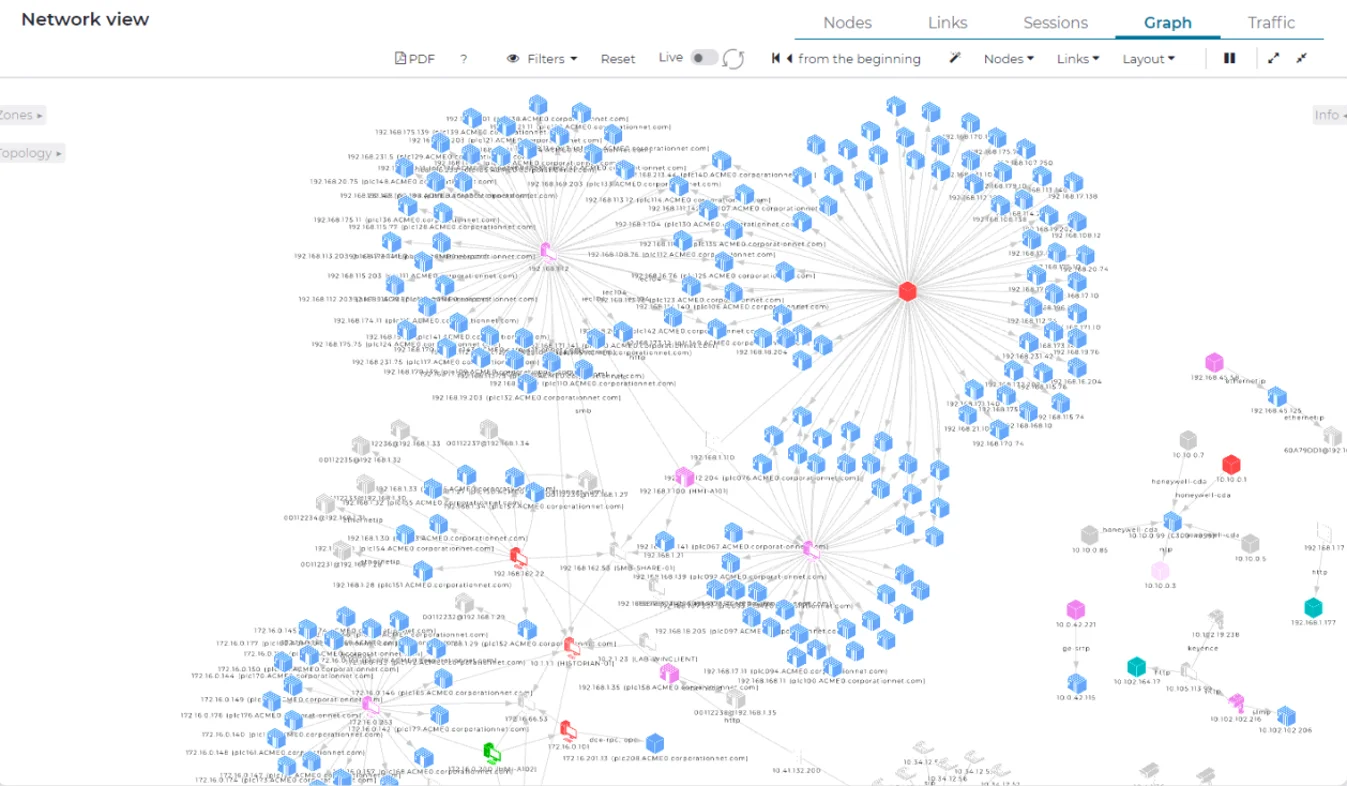
Infrastructure Security
Automatically track your ICS, OT, IT and IoT/IIoT assets. Immediately see your entire network. Drill down for extensive node information including name, type, serial number, firmware version and components.